Date: 2025-12-13
Timeframe reviewed: 2025-06-01 → 2025-12-13
Executive Summary
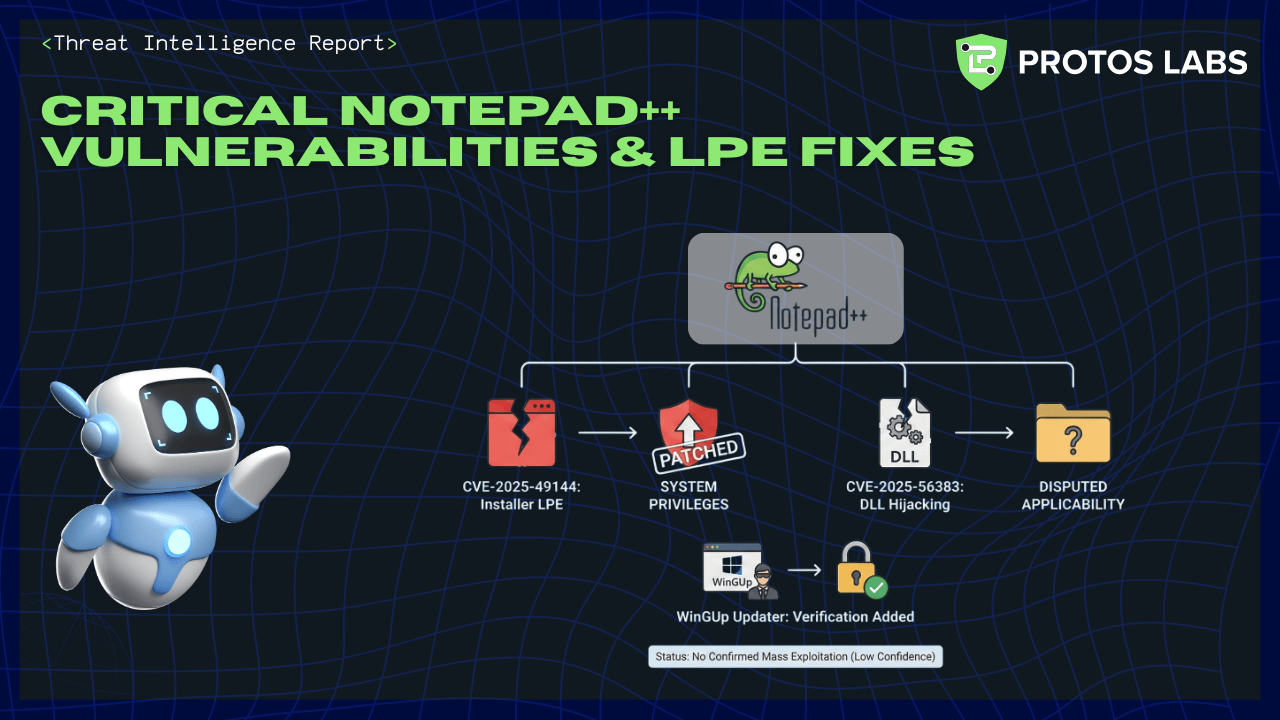
- Two Notepad++ vulnerabilities investigated: CVE-2025-49144 (installer uncontrolled executable search path → LOCAL PRIVILEGE ESCALATION) and CVE-2025-56383 (DLL HIJACKING / binary planting). Both have public ADVISORIES and public POC materials.
- CVE-2025-49144: Confirmed INSTALLER LPE that can yield NT AUTHORITY\SYSTEM when attackers place a malicious executable in the install working directory. Vendor patched installer calls to fully-qualified system paths. CONFIDENCE: HIGH.
- CVE-2025-56383: Public POC demonstrates DLL replacement to execute code if Notepad++ is installed to a user‑writable directory. Applicability to default Program Files installs is DISPUTED by maintainers. CONFIDENCE: HIGH (POC) / MEDIUM (applicability).
- WinGUp updater: Vendor introduced signature/certificate verification after reports of update traffic redirection. Investigation of root cause ongoing. CONFIDENCE: MEDIUM.
- No authoritative public telemetry confirming large‑scale active exploitation during the review window. CONFIDENCE (mass exploitation): LOW.
Technical Findings (concise)
- CVE-2025-49144: Installer invoked regsvr32/rundll32 without a fully-qualified path, enabling binary planting in Downloads → SYSTEM on installer run. CVSS 3.x: 7.3 (HIGH). Fix: vendor commit to prepend system path (commit referenced).
- CVE-2025-56383: DLL search-order hijack via plugin DLL replacement (e.g., NppExport[.]dll). POC available. Risk depends on install location permissions; vendor disputes default-install exposure.
- Updater (WinGUp): Signature validation added in later vendor releases; recommended to validate update binary signatures and remove legacy root certs if vendor instructs.
POC & Observed Abuse
- POCs for both CVEs exist on public code hosting platforms. POCs demonstrate practical exploit flows in lab conditions.
- Observed community reporting and some media coverage; no confirmed broad in‑the‑wild exploitation telemetry from major vendors in open sources at time of review.
DEFANGED IOCs (selected)
- CVEs: CVE-2025-49144, CVE-2025-56383
- ADVISORIES / REPOS (DEFANGED):
- hXXps://nvd[.]nist[.]gov/vuln/detail/CVE-2025-49144
- hXXps://nvd[.]nist[.]gov/vuln/detail/CVE-2025-56383
- hXXps://github[.]com/notepad-plus-plus/notepad-plus-plus/security/advisories/GHSA-fq6p-2qgq-54m8
- hXXps://notepad-plus-plus[.]org/news/v889-released/
- hXXps://github[.]com/zer0t0/CVE-2025-56383-Proof-of-Concept
- Filenames/paths to monitor (DEFANGED): notepadpp_installer[.]exe, malicious_helper[.]exe, regsvr32_loader[.]c, notepad_plugin_scintilla[.]dll, %USERPROFILE%\\Downloads\\, C:\\Program Files\\Notepad++\\plugins\\.dll
Detection & Response — High-Level
- Hunt for installer→child executions where child path is %USERPROFILE%\\Downloads or %USERPROFILE%\\Desktop (Sysmon EID=1 / EDR process-create).
- Alert on regsvr32/rundll32 execution from non-system paths; block execution from user profile folders if possible.
- Monitor ModuleLoad events: notepad++.exe loading DLLs from user dirs or %TEMP%.
- Enforce code-signature checks on installers/updates; monitor TLS certs and SNI for update downloads.
Remediation & Prioritized Actions
- PATCH: Apply vendor-patched Notepad++ releases (vendor-published patched versions; apply the latest). HIGH priority.
- PREVENT: Block execution of unsigned installers from user-writable folders (SRP/AppLocker/WDAC). HIGH priority.
- HARDEN: Enforce installs to Program Files with admin-only write permissions; remove legacy Notepad++ root certs if vendor directs.
- HUNT: Run EDR hunts for installer-child-from-downloads and notepad++ DLL loads from user paths; remediate as needed.
- ARCHIVE: In a secure lab, clone POC repos, compute hashes, and derive detection signatures (YARA/SIEM rules).
Confidence & Gaps
- Core vulnerability mechanics and vendor fixes: HIGH confidence.
- POC existence: HIGH confidence.
- Applicability of CVE-2025-56383 to default installs: MEDIUM (DISPUTED).
- Evidence of broad exploitation: LOW (no public vendor/EDR telemetry found).
- Gap: Archive of all POC repo files and enterprise EDR telemetry would improve confidence on active exploitation.
MITRE ATT&CK MAPPING (TECHNIQUE IDs)
Below is the MITRE ATT&CK mapping table integrated into this FINAL REPORT. The table maps TACTICS → TECHNIQUES (with MITRE TECHNIQUE IDs), DESCRIPTIONS (how they map to the Notepad++ CVEs/POCs), DETECTION ideas, and MITIGATIONS. All IOCs in the table are DEFANGED.
TACTIC
TECHNIQUE (NAME)
TECHNIQUE ID
DESCRIPTION (Mapping to CVE / POC)
DETECTION / HUNT IDEAS
MITIGATION / RESPONSE
INITIAL ACCESS
User Execution: Malicious File
T1204.002
Victim runs Notepad++ installer or repackaged installer from Downloads/Desktop — POC for CVE-2025-49144 depends on user execution.
Alert on ProcessCreate where parent = browser/download helper and ChildImage path contains %USERPROFILE%\\Downloads or %USERPROFILE%\\Desktop (Sysmon EID=1).
Block execution from user-writable folders (SRP/AppLocker/WDAC); use managed package distribution; user awareness.
EXECUTION
Signed Binary Proxy Execution (regsvr32)
T1218.010
Installer invoked regsvr32 without full path; OS resolves malicious regsvr32 in working dir → execution during install (CVE-2025-49144 POC).
Detect regsvr32.exe or rundll32.exe launched from non-system paths (ImagePath not like %WINDIR%\\System32). Correlate parent = installer.
Vendor patch uses $winSysDir\\regsvr32.exe; block regsvr32/rundll32 from user dirs; enforce execution policies.
PERSISTENCE
DLL Search Order Hijacking
T1574.001
POC demonstrates replacing plugin DLLs (e.g., NppExport[.]dll) so notepad++.exe loads malicious code (CVE-2025-56383).
ModuleLoad events: detect notepad++.exe loading DLLs from %USERPROFILE% or %TEMP%; file integrity checks for plugin DLLs.
Enforce install to Program Files (admin-only write); verify DLL signatures; whitelist vendor-signed DLLs.
PRIVILEGE ESCALATION
Exploitation for Privilege Escalation
T1068
Binary planting in installer leads to elevation to SYSTEM (CVE-2025-49144 POC resulted in SYSTEM reverse shell).
Hunt for processes spawned by installers that escalate to SYSTEM or for SYSTEM-level shells started by non-admin parents.
Apply patches; restrict installer execution sources; isolate/remediate compromised hosts.
DEFENSE EVASION
Masquerading
T1036
Malicious helper or forged DLLs mimic legitimate names (regsvr32, NppExport[.]dll) to evade trivial checks.
Detect signature mismatches and unexpected file paths for expected binaries; flag unexpected filenames in Program Files.
Enforce code-signing checks; block unsigned binaries in protected folders; maintain baseline hashes.
PERSISTENCE
Create or Modify System Process (Service)
T1543
Post-exploit behaviors may install services or system processes after achieving SYSTEM.
Alert on new/modified service creation events; verify service binary path legitimacy.
Monitor/deny unauthorized service creation; forensic image isolated hosts and remove persistence.
PERSISTENCE
Scheduled Task
T1053
Adversary may create scheduled tasks for persistence after escalation.
Detect Scheduled Task creation by installers or unexpected accounts; hunt for tasks created near installer execution times.
Block unauthorized task creation via policy; monitor task creation events.
COMMAND & CONTROL
Application Layer Protocol (reverse shell)
T1071
POC demonstrates reverse shell after escalation; attacker may use common protocols for C2.
Detect unusual outbound connections (long-lived/non-standard endpoints) from workstations; inspect for reverse-shell patterns.
Egress filtering, proxying, IDS signatures for C2, isolate infected hosts.
INITIAL ACCESS / PERSISTENCE
Supply Chain / Update Hijack (Updater abuse)
T1195 (and T1553 sub-techniques)
WinGUp update redirection reports — attacker could deliver malicious update binary in absence of signature verification.
Monitor update-download TLS certs (SNI/SubjectCN) and domains; detect signature verification failures in updater logs.
Enforce signature verification of update binaries; use managed update channels; restrict updater network egress; remove deprecated root certs if vendor instructs.
DEFENSE EVASION
Abuse Elevation Control Mechanism / Signed Binary Proxy
T1548 / T1218
Use of legitimate OS utilities or signed binaries to execute payloads and bypass controls.
Correlate unexpected use of signed system utilities (regsvr32, rundll32) by non-standard parents; detect signed binary executed from unexpected locations.
Block signed-binary abuse via AppLocker/WDAC rules; limit signed binaries runnable by non-admins.
Notes:
- TECHNIQUE IDs are MITRE ATT&CK canonical IDs (e.g., T1204.002). Use these IDs to map detections to SOC/TTP taxonomies.
- All IOCs above are DEFANGED. Replace defanging only in controlled SOC ingestion contexts.
- Detection efficacy assumes presence of telemetry (SYSLOG/SYSMON, EDR ModuleLoad/ProcessCreate/FileCreate, network TLS metadata). If telemetry is limited, prioritize host hardening and patching.
Appendix — Quick Action Checklist
- Patch endpoints to vendor-patched Notepad++ (apply latest).
- Block unsigned installers from running in user-writable folders.
- Hunt for installer→child-from-Downloads and notepad++ DLL loads from user dirs.
- Archive POC repos in an isolated lab and compute hashes to add to detection lists.
- Validate update-signing enforcement for WinGUp and remove legacy root certs if vendor instructs.