Classification: TLP:CLEAR
Analyst: AI Threat Intelligence
Executive Summary
| Attribute |
Value |
| Risk Level |
HIGH |
| Key Finding |
Spear-phishing delivered a VBA-based dropper that installs a Rust-based RAT (“RustyWater”)
which performs process injection, registry persistence, and HTTP JSON C2 to
nomercys[.]it[.]com (resolved in sandboxes to 159[.]198[.]66[.]153).
|
| Primary Action |
Immediately block the listed hashes, domain, and IP at perimeter controls and begin hunting for
CertificationKit.ini and macro artifacts across endpoints.
|
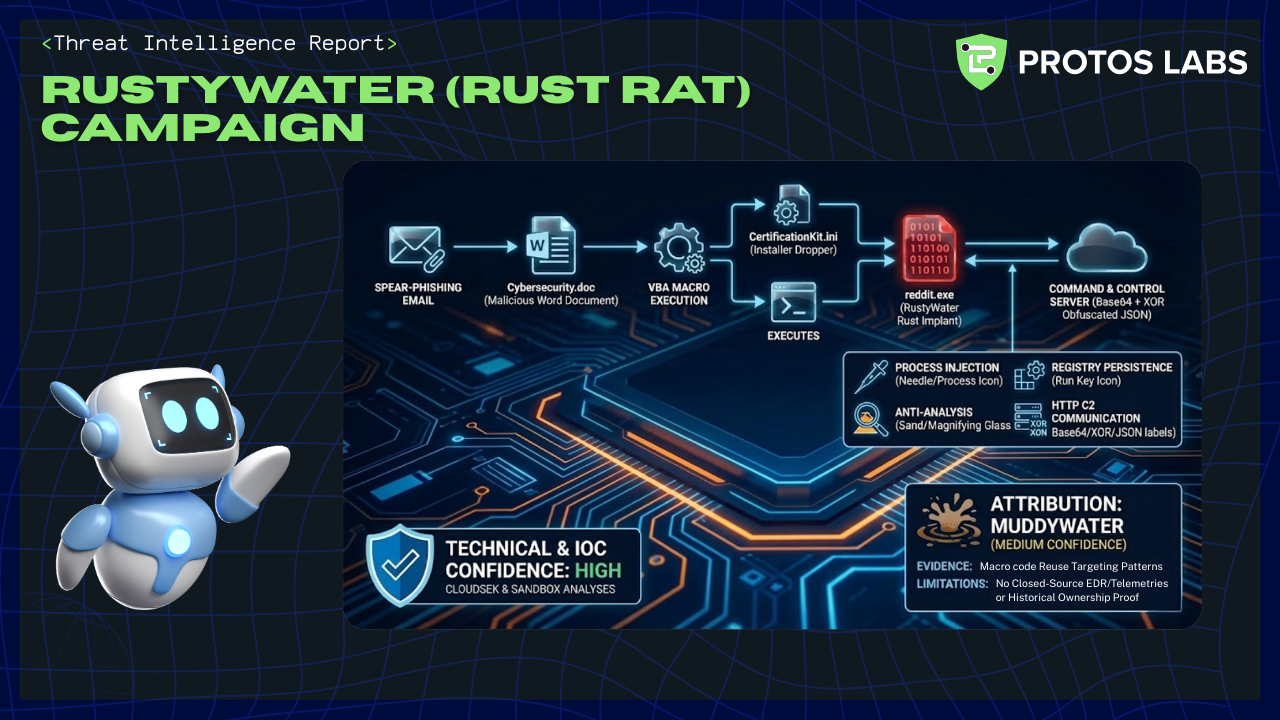
CloudSEK's public disclosure and multiple sandbox analyses corroborate a targeted spear-phishing campaign delivering a Rust-compiled remote access implant (RustyWater) via a malicious Word document (Cybersecurity.doc) containing an embedded VBA macro that writes and executes a dropped installer (CertificationKit.ini) which in turn launches a Rust PE (reddit.exe). The implant exhibits process injection, registry Run-key persistence, anti-analysis measures, and an HTTP-based JSON C2 employing Base64 and lightweight XOR obfuscation. These technical findings and core IOCs are supported at High confidence by vendor reporting and sandbox evidence.
Attribution to the threat actor MuddyWater is assessed at Medium confidence: CloudSEK links macro code reuse (unique function names) and targeting patterns consistent with MuddyWater, but closed-source EDR/telemetry and historical registrant/ownership proof were not available in the reviewed artifacts to elevate confidence to High.
Investigation Objective & Methodology
Original Question: Please do a Deep Dive analysis for this news: "MuddyWater Launches RustyWater RAT via Spear-Phishing Across Middle East Sectors" (from Investigation Objective)
Scope: Open-source confirmation and technical analysis of the reported campaign; extraction and enrichment of IOCs (domains, IPs, URLs, hashes, email addresses); infrastructure enrichment (DNS/WHOIS/hosting where available); technical analysis of RustyWater capabilities; correlation with known MuddyWater TTPs for attribution assessment.
Timeframe: Last 30 days (approx. 2025-12-12 to 2026-01-11)
Sources Used: Vendor write-up (CloudSEK), public sandbox analyses (ANY.RUN, JoeSandbox), MalwareBazaar sample listings, VirusTotal metadata and the artifacts provided for this investigation (research_findings.md, enriched_iocs.md, infrastructure_analysis.md, malware_actor_correlation.md, intelligence_analysis.md, fact_check.md).
Methodology: Triangulate vendor disclosure with public sandbox behavior and sample repositories; validate IOCs present in CloudSEK appendix against sandbox PCAPs and MalwareBazaar entries; assess technical behaviors from static and dynamic analyses documented in sandboxes; evaluate attribution claims against code-level fingerprints and infrastructure patterns; note limitations where closed-source telemetry or WHOIS/passive-DNS yields were absent.
Key Findings (Evidence-based)
High Confidence Findings
- Delivery: The campaign used a malicious Word document named Cybersecurity.doc with embedded VBA macro that decodes a hex blob and writes/executes a dropped installer (CertificationKit.ini). Evidence: CloudSEK disclosure and sandbox runs. (Confidence: HIGH) — supporting artifact: RustyWater (reddit.exe) and associated samples documented in the references below.
- Malware capabilities: The Rust PE (reddit.exe) implements asynchronous networking using Rust crates (reqwest/tokio), performs process injection (targeting explorer.exe), sets persistence via a Registry Run key pointing to CertificationKit.ini, and contains anti-analysis (VEH handler) behaviors; C2 protocol is HTTP JSON with Base64 and a lightweight XOR obfuscation layer. (Confidence: HIGH) — see nomercys[.]it[.]com and sample hashes below.
- IOCs / Infrastructure: Sandbox PCAPs and MalwareBazaar link the implant to domain nomercys[.]it[.]com resolving to IP 159[.]198[.]66[.]153. A characteristic GET for /favicon.ico from the dropped binary is documented in sandbox captures. (Confidence: HIGH)
Medium Confidence Findings
- Attribution: CloudSEK attributes the campaign to the MuddyWater intrusion set based on VBA macro code reuse (function names such as WriteHexToFile / love_me) and targeting overlap; this attribution is plausible but lacks closed-source telemetry in the reviewed artifacts to reach High. (Confidence: MEDIUM) — see MuddyWater and analysis in the Evidence section.
- Supporting infrastructure: Additional campaign domains (Cloudflare-fronted) include stratioai[.]org and bootcamptg[.]org; associated IP pivots include sample hashes and IPs (see IOC Annex). (Confidence: MEDIUM-HIGH)
Detailed Technical Analysis
Delivery
- Vector: Spear-phishing email with attachment. Lure subject reported as "Cybersecurity Guidelines" and sender impersonation observed for info[@]tmcell. The attached Word document Cybersecurity.doc contains an embedded VBA macro that stores a long hex blob within a UserForm (UserForm1.TextBox1) and decodes it to write CertificationKit.ini to C:\ProgramData, then executes it. Evidence: CloudSEK writeup and sandbox runs. (Confidence: HIGH) — see email artifact MuddyWater (for attribution context) and mail sender info[@]tmcell.
Malware Capabilities
- Loader chain: VBA macro -> CertificationKit.ini (dropped installer) -> reddit.exe (Rust PE). (Confidence: HIGH) f38a56b8dc0e8a5... (doc hash) and 7523e53c979692f9eecf... (reddit.exe hash).
- Execution & Evasion: Binary contains VEH-based anti-debug handlers and anti-EDR scanning heuristics observed in sandboxes. (Confidence: HIGH) RustyWater (reddit.exe).
- Privilege / Lateral: The implant performs process injection using VirtualAllocEx/WriteProcessMemory into explorer.exe, enabling code execution in a trusted process. (Confidence: HIGH) RustyWater (reddit.exe).
- Persistence: Registry Run key pointing to C:\ProgramData\CertificationKit.ini observed in sandbox artifacts; primary persistence mechanism is the Run key. (Confidence: HIGH) — see CertificationKit[.]ini.
Command & Control (C2)
- Protocol: HTTP-based JSON payloads. Payload fields include Base64-encoded content which is XOR-obfuscated at the byte level. The implant performs an initial GET of /favicon.ico followed by JSON exchanges over HTTP to the C2 host. (Confidence: HIGH) — observed in ANY.RUN and JoeSandbox PCAPs targeting nomercys[.]it[.]com -> 159[.]198[.]66[.]153).
MITRE ATT&CK Mapping (Observed)
| TACTIC |
TECHNIQUE (ID) |
OBSERVED ACTIONS / EVIDENCE |
DETECTION OPPORTUNITIES |
MITIGATIONS / CONTROLS |
CONFIDENCE |
| Initial Access |
Spearphishing Attachment
(T1566.001)
|
Malicious Word attachment Cybersecurity.doc with embedded VBA; subject “Cybersecurity Guidelines”; sender impersonation info[@]tmcell. |
Mail gateway sandboxing; attachment static scanning; detect long embedded hex blobs in VBA; mailbox rules for suspicious subject/sender combos. |
Block/strip high-risk attachments or detonate in sandbox; enforce attachment blocking for risky types; phishing training; enable DMARC/SPF/DKIM validation. |
HIGH |
| Execution / User Execution |
Malicious Macros
(T1204.002)
|
VBA stores long hex in UserForm1.TextBox1 and decodes/writes binary (WriteHexToFile / love_me routine); macro writes CertificationKit.ini then executes it. |
Detect macros with long hex blobs; YARA on macro text; monitor Office writing to C:\\ProgramData or spawning cmd/wscript/powershell. |
Disable macros by default; enforce Protected View; mail attachment sanitization; block known macro patterns via mail/EDR. |
HIGH |
| Persistence |
Registry Run Keys / Startup Folder
(T1547.001)
|
Run key created pointing to C:\\ProgramData\\CertificationKit.ini. |
Alert on new Run key entries; detect uncommon processes launched from C:\\ProgramData. |
Monitor/alert Run key changes; restrict writes to startup registry keys; apply application control/whitelisting. |
HIGH |
| Defense Evasion |
Virtualization/Sandbox Evasion
(T1497)
|
VEH-based anti-debug handlers and anti-EDR heuristics observed in Rust binary. |
Behavioral telemetry for anti-debug API usage; confirm in detonation/sandbox reports; look for early exit conditions. |
Tune EDR for anti-debug patterns; keep EDR updated; cross-correlate host + network telemetry to detect evasive implants. |
HIGH |
| Privilege Escalation / Defense Evasion |
Process Injection
(T1055)
|
VirtualAllocEx / WriteProcessMemory into explorer.exe observed in dynamic analysis. |
EDR rules for injection sequences: VirtualAllocEx → WriteProcessMemory → CreateRemoteThread; monitor suspicious parent/child process lineages. |
Block/alert on injection patterns; strong application control; reduce local privileges to limit blast radius. |
HIGH |
| Command & Control |
Application Layer Protocol: Web (HTTP/S)
(T1071.001)
|
HTTP JSON C2 with Base64 + XOR obfuscation; initial GET /favicon.ico then JSON exchanges to nomercys[.]it[.]com → 159[.]198[.]66[.]153. |
Proxy/NGFW: detect /favicon.ico beaconing to unusual domains; inspect JSON bodies for Base64 fields; IDS patterns for XOR-like entropy. |
Block/limit HTTP egress; enforce proxy controls (TLS inspection if feasible); sinkhole/blackhole confirmed malicious domains. |
HIGH |
| User Execution / C2 Support |
User Execution
(T1204)
/
Application Layer Protocol
(T1071)
|
User opens doc and enables macros → file dropper → process execution → outbound HTTP comms and potential data access/exfil. |
Chain correlation: email delivery → macro execution → file write (C:\\ProgramData) → process spawn → DNS/HTTP C2. |
Multilayer hunting across mail/EDR/proxy; isolate infected hosts; reset creds; investigate lateral movement opportunities. |
HIGH |
Attribution Assessment
- Attribution claim: MuddyWater is the likely actor behind this campaign per CloudSEK. (Working hypothesis: MuddyWater)
- Confidence: MEDIUM.
- Rationale:
- Supporting evidence: Code-level fingerprints in VBA macros (function names such as WriteHexToFile and love_me) and targeting of Middle East diplomatic/maritime/telecom sectors mirror historically observed MuddyWater tradecraft; CloudSEK documents these linkages. (Source: malware_actor_correlation.md; research_findings.md)
- Limitations: No closed-source EDR telemetry, historical owner registrant proofs, or vendor-provided long-term telemetry were present in the reviewed artifacts to definitively tie infrastructure and code to MuddyWater. Opportunistic hosting (Namecheap, Cloudflare fronting) is common across many actors and therefore not uniquely identifying. (See Fact Check & Gaps.)
- Assessment: Treat attribution to MuddyWater as a plausible working hypothesis (MEDIUM). Use it to prioritize hunting in relevant sectors and geographies, but avoid public attribution statements requiring High confidence until closed-source telemetry or definitive infrastructure ownership links are obtained.
Recommendations & Mitigation
Immediate Actions (Priority 1) 🚨
| # |
Action |
Rationale |
| 1 |
Block and quarantine the confirmed malicious SHA-256 hashes at file/endpoint controls (see IOC Annex). |
Prevent execution and lateral spread from known samples (HIGH confidence). |
| 2 |
Block DNS resolution and HTTP(S) egress to nomercys[.]it[.]com and 159[.]198[.]66[.]153. |
Disrupt C2 communications observed in sandbox PCAPs (HIGH confidence). |
| 3 |
Quarantine / isolate hosts found with CertificationKit[.]ini on disk or Run key entries pointing to it. |
Prevent re-execution of the persistent payload (HIGH confidence). |
Short-term Actions (Priority 2) ⚠️
| # |
Action |
Rationale |
| 1 |
Hunt EDR telemetry for: process injection into explorer.exe, execution of reddit.exe,
registry Run keys pointing to CertificationKit[.]ini, and execution chains originating from
Cybersecurity.doc macro activity.
|
Identify compromised hosts and scope the incident (HIGH confidence).
|
| 2 |
Search mail gateway logs for inbound messages with subject "Cybersecurity Guidelines" and sender
info[@]tmcell; inspect attachments for VBA macro patterns
(WriteHexToFile, love_me).
|
Identify potential recipients and initial access events
(HIGH confidence for macro/hunt rules; sender impersonation is MEDIUM confidence).
|
| 3 |
Collect and preserve sandbox PCAPs and sample files for deeper reverse engineering; forward to vendor partners
for closed-source telemetry correlation.
|
Required to validate attribution and expand IOC sets (MEDIUM→HIGH confidence).
|
Long-term Improvements (Priority 3) 🎯
- Create YARA rules for the VBA macro pattern (embedded long hex blob + WriteHexToFile / love_me) and for Rust binary static markers (reqwest/tokio strings, XOR-base64 framing). (Actionable for proactive detection across mail and endpoint stores.)
- Implement enhanced mail attachment detonation workflows for high-risk attachments and automated extraction of macro function names/signatures for rapid triage.
- Re-run WHOIS/passive DNS and certificate transparency (crt.sh) lookups periodically to capture historical pivots and registrant changes.
Detection Opportunities 🔍
- Proxy/NGFW signatures: Detect and flag HTTP GET to hXXps://nomercys[.]it[.]com/favicon[.]ico and subsequent JSON POSTs with Base64 fields. Capture headers and user-agent strings for further pivoting. (HIGH confidence)
- EDR behavioral detections: Monitor for VirtualAllocEx/WriteProcessMemory/CreateRemoteThread sequences originating from reddit[.]exe or processes spawned from C:\ProgramData\CertificationKit[.]ini. (HIGH confidence)
- Mail gateway rules: Heuristics for embedded long hex blobs in VBA UserForm controls and macro function names WriteHexToFile / love_me. (HIGH confidence for pattern; MEDIUM for sender-based detection)
- YARA examples (starting points): match strings for "reqwest" / "tokio" in PE string table and VBA function names; match embedded long hex decode routine structure in macro text. (Use sandbox artifacts to refine rules.)
IOC Annex (defanged)
| Type |
Indicator (Defanged) |
Context |
Confidence |
| Domain |
nomercys[.]it[.]com |
C2 / favicon host observed in sandbox PCAPs |
HIGH |
| IP |
159[.]198[.]66[.]153 |
Resolved from nomercys[.]it[.]com in sandbox traffic |
HIGH |
| Domain |
stratioai[.]org |
Cloudflare-fronted infrastructure |
MEDIUM–HIGH |
| Domain |
bootcamptg[.]org |
Cloudflare-fronted infrastructure |
MEDIUM–HIGH |
| IP |
(see sample hashes below) |
— |
— |
| IP |
159[.]198[.]68[.]25 |
Host observed in CloudSEK appendix (stratioai[.]org) |
MEDIUM–HIGH |
| IP |
161[.]35[.]228[.]250 |
DigitalOcean-hosted pivot in appendix |
MEDIUM–HIGH |
| Email |
info[@]tmcell |
Impersonated sender in lure |
MEDIUM |
| Filename |
Cybersecurity[.]doc |
Malicious lure document |
HIGH |
| Filename |
CertificationKit[.]ini |
Dropped installer path C:\\ProgramData\\ |
HIGH |
| Filename |
reddit[.]exe |
Rust PE launched by installer |
HIGH |
| SHA256 |
f38a56b8dc0e8a581999621eef65ef497f0ac0d35e953bd94335926f00e9464f |
Cybersecurity.doc sample (MalwareBazaar) |
HIGH |
| SHA256 |
7523e53c979692f9eecff6ec760ac3df5b47f172114286e570b6bba3b2133f58 |
reddit.exe sample (MalwareBazaar) |
HIGH |
Note: Additional SHA256s from CloudSEK appendix are available in the source artifacts and enrichment CSV and are categorized MEDIUM/CRITICAL in enrichment; incorporate those into blocking/hunting as appropriate. (See Evidence & Sources.)
Confidence & Limitations
High Confidence:
- Delivery chain (malicious Word doc -> VBA macro -> CertificationKit[.]ini -> reddit[.]exe) and the core malware behaviors (process injection, registry Run-key persistence, HTTP JSON C2 with Base64 + XOR, use of Rust crates) are strongly supported by CloudSEK and multiple sandbox analyses. (Cited in research_findings.md, enriched_iocs.md, malware_actor_correlation.md)
Medium Confidence:
- Attribution to MuddyWater based on macro code reuse and targeting is plausible but lacks closed-source telemetry and registrant/ownership proofs in the reviewed artifacts. Use as a working hypothesis. (Cited in malware_actor_correlation.md and intelligence_analysis.md)
Limitations / Gaps:
- Closed-source telemetry (enterprise EDR logs, historical vendor YARA hits, long-term infrastructure ownership) was not available in the provided artifacts—this prevents elevating attribution confidence to High. (Fact check and analysis artifacts document these gaps.)
- WHOIS/passive-DNS/CRT.sh/ASN queries were not fully retrieved during enrichment due to collection limitations; re-running these queries is recommended. (See infrastructure_analysis.md and fact_check.md)
Evidence & Sources
Primary artifacts used in this report (selected):
- Vendor write-up: CloudSEK — "Reborn in Rust: Muddy Water Evolves Tooling with RustyWater Implant" (primary disclosure and IOC appendix). See research_findings.md and intelligence_analysis.md for summary.
- Sandbox & sample repositories: MalwareBazaar entries and ANY.RUN / JoeSandbox analyses for Cybersecurity.doc and reddit.exe (see enriched_iocs.md and research_findings.md).
- IOC Enrichment: enriched_iocs.md (hash reputations, hosting, VT links)
- Threat context & attribution discussion: malware_actor_correlation.md
- Validation & confidence weighting: reviews/fact_check.md and reviews/intelligence_analysis.md
Prepared by: AI Threat Intelligence